Introduction:
AIDA64 Extreme is a powerful PC diagnostic tool designed for advanced users and IT professionals who seek to maximize their system's performance and stability. This tool provides in-depth real-time monitoring and extensive information about your hardware, software, and system health, making error identification and troubleshooting remarkably efficient.Main Features:
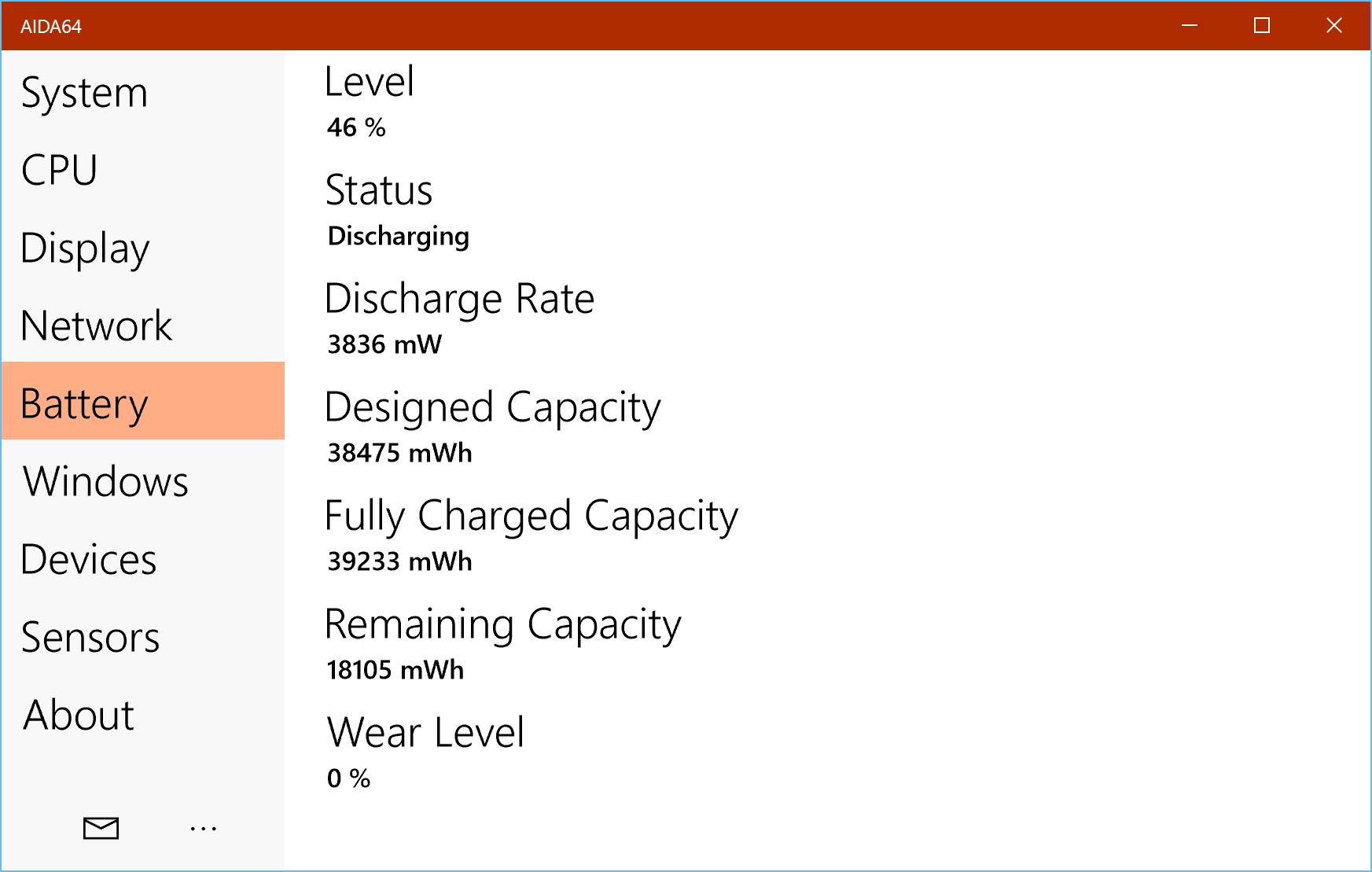
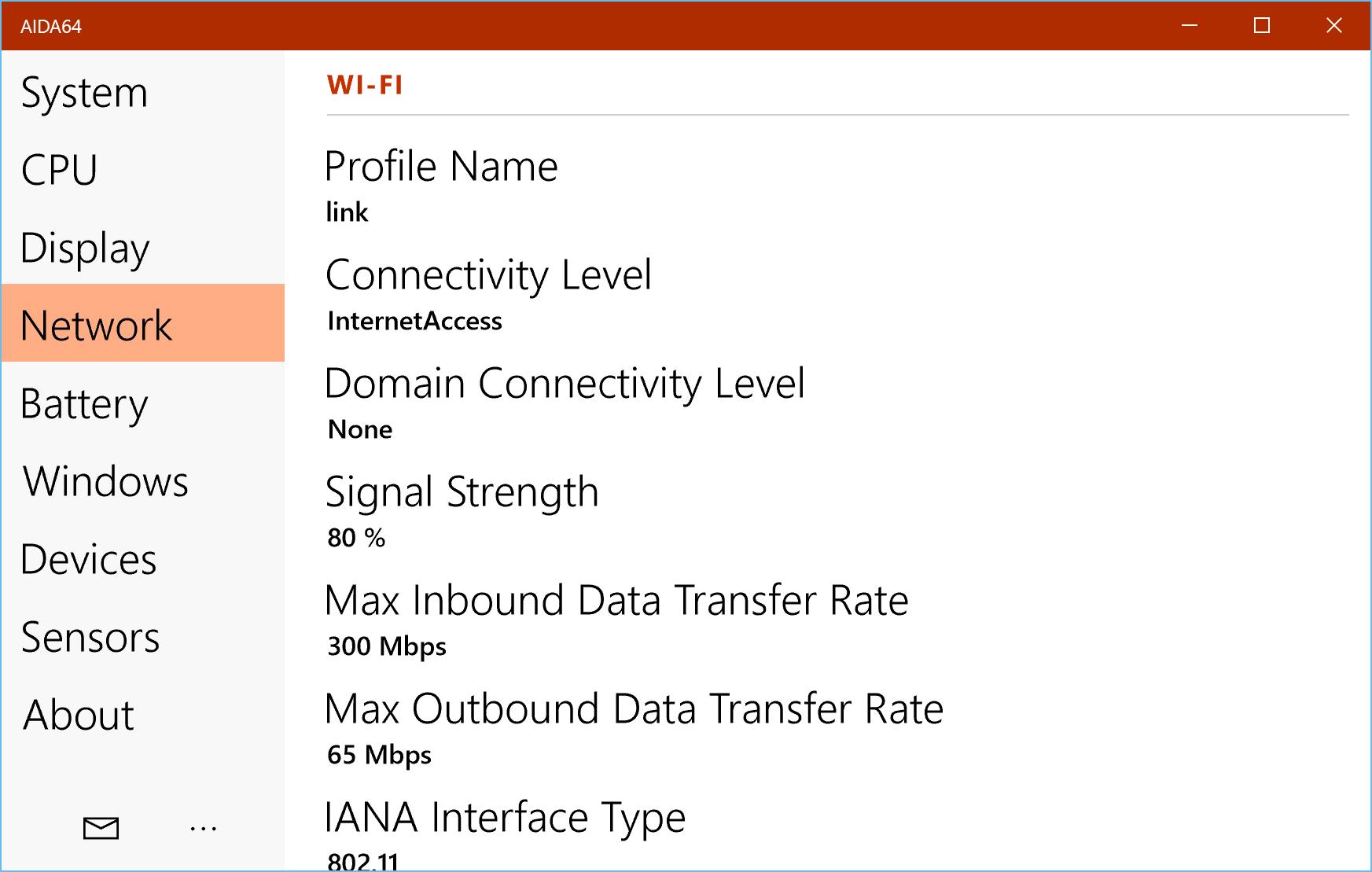
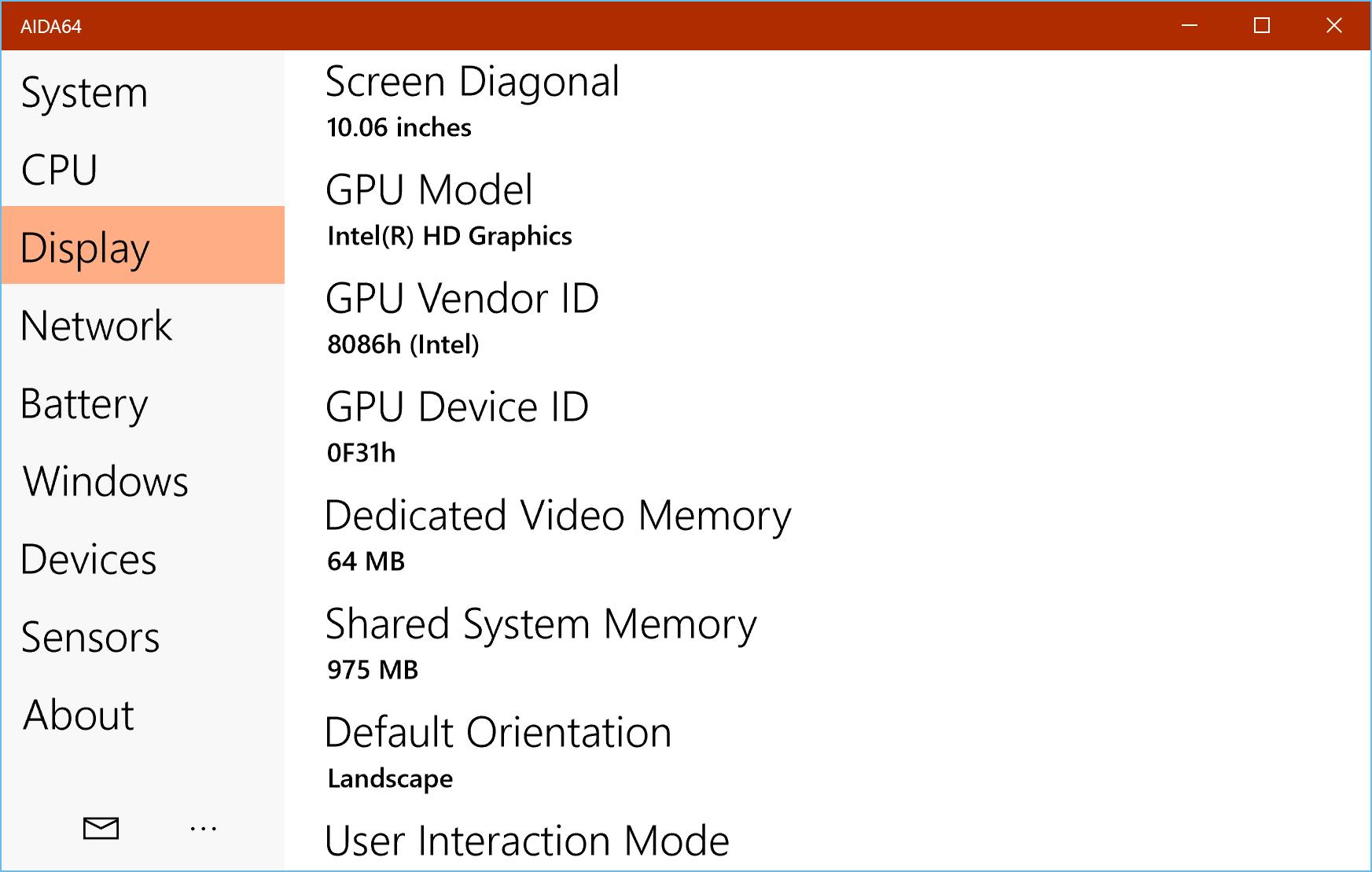
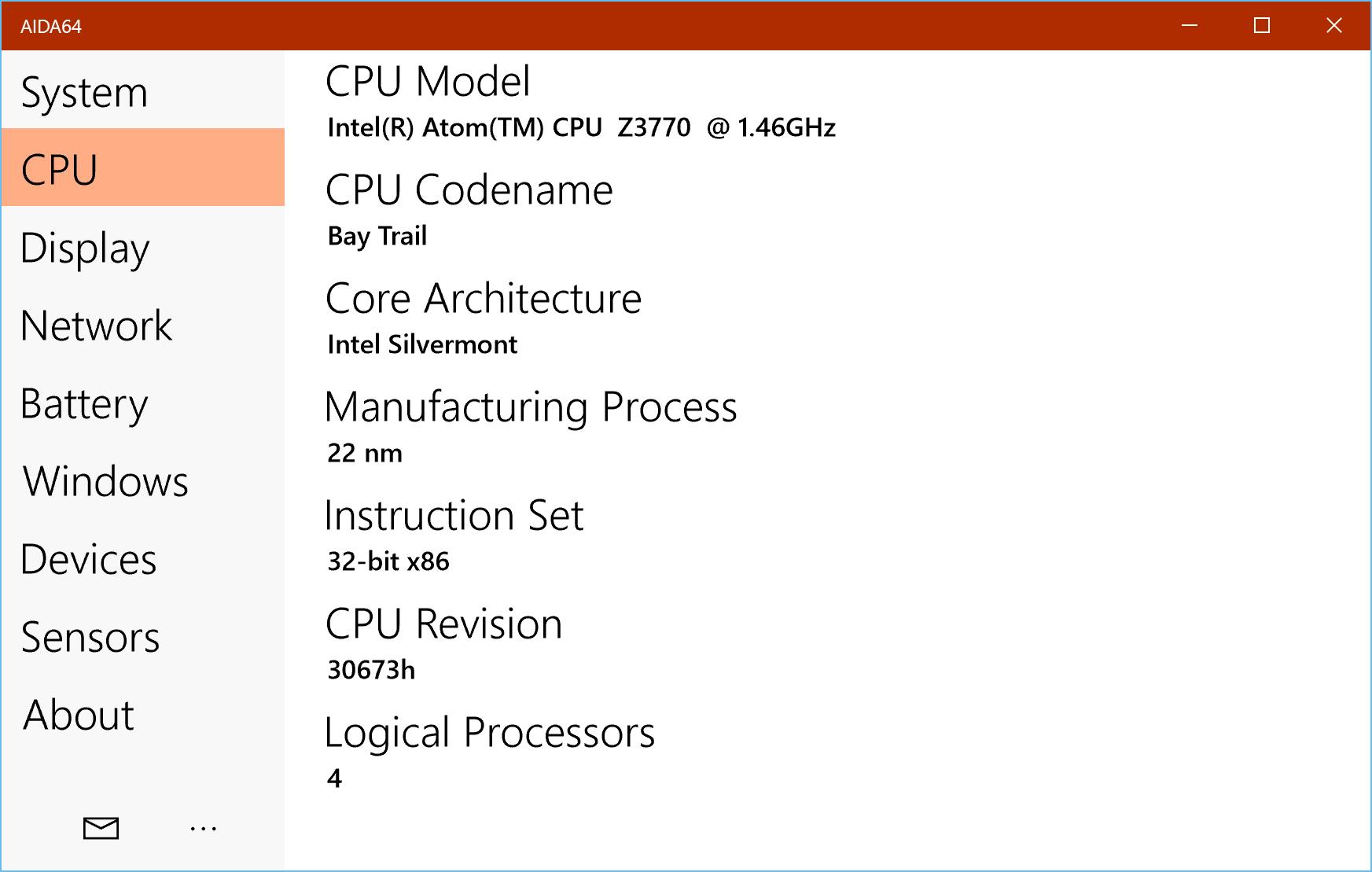
- Comprehensive Diagnostics: AIDA64 Extreme offers detailed insights into components such as CPU, BIOS, operating system, running services, monitor, and hard drives, ensuring no aspect of your system is overlooked.
- Extensive Database: Leverage a staggering database of over 120,000 entries for accurate hardware detection, enabling easy identification and management of all connected elements.
- User-Friendly Interface: Navigate through various tabs effortlessly for a thorough understanding of your PC’s performance.
- Real-Time Monitoring: Keep an eye on system health and performance metrics with real-time feedback, alerting you to potential issues before they escalate.
Customization:
AIDA64 Extreme allows users to personalize their experience by adjusting the interface and configuring settings to focus on the specific parameters they wish to monitor. You can choose which metrics to display and how they are presented, tailoring the diagnostic experience to your needs.Modes/Functionality:
- Diagnostic Mode: Easily locate and troubleshoot system errors and performance issues with a single click, promoting quick resolutions to maintain system health.
- Benchmarking Tools: Utilize the built-in benchmarking tools to assess your system's performance across various metrics, ensuring you stay informed about your hardware capabilities.
- Benchmark Scores: Compare your results with global standards and gain insights into how your setup ranks against similar systems.
Pros and Cons:
Pros:
- In-depth diagnostic capabilities covering all system components.
- Impressive database with extensive hardware identification capability.
- User-friendly interface that simplifies complex data presentations.
- Real-time monitoring and alerts enhance system maintenance.
Cons:
- May overwhelm novice users due to its extensive features.
- Advanced benchmarking tools may require a learning curve.
Discover more apps
MagiKart: Retro Kart Racing lets you race as various characters, using customizable controls and special items, evoking nostalgia reminiscent of Super Mario Kart.
LunaProxy offers stable residential proxies for social media, with 200 million devices, dynamic pricing, 99.9% uptime, easy API integration, and a profitable affiliate program.
Genius DLL is an easy-to-use application for quickly downloading and registering DLLs, requiring just a few clicks to search, download, and manage libraries.
The Quick Start tab in Google Chrome provides access to installed apps, including a shortcut for iCloud Reminders, enhancing user convenience despite being unofficial.
Tiger Password Recovery is a user-friendly tool that efficiently retrieves lost passwords across various applications and devices using advanced algorithms.
Desktop Gadgets Revived restores classic Windows desktop gadgets, allowing customization with functional and aesthetic widgets on modern operating systems, maintaining compatibility and nostalgic design.
Advanced BAT to EXE Converter transforms BAT files into EXE format, enhancing application protection and aesthetics while allowing versioning and password features for developers.
Renee File Protector is a tool that easily hides and locks files on your computer or external devices, ensuring sensitive information remains secure.